Voice Biometrics: Why Businesses and Users are driving its adoption
In this blog post, we’ll look at the rapidly growing market of Voice Biometrics, and what drives its increasing rate of adoption, as more businesses and services are made aware of the need for multi-factor authentication.
Why is Voice Biometrics needed?
Today’s cybercriminals are masters of disguise. This means that companies, businesses and services need to shore up their security perimeters using more complex methods of identification and authentication than the old standard of passwords and PINs.
As the way we use our devices changes in response to different needs and demands, there has been an exponential growth in the interconnections between the devices and accounts we use to navigate the online world. We now expect seamless interaction, flowing through cyberspace with ease. However, convenience has traditionally led to insecurity- and data is becoming increasingly valuable whilst AI algorithms learn our online activities to offer us tailored services. This has led a significant rise in potential security vulnerabilities, and subsequently, a sharp, concurrent rise in cybercrime.
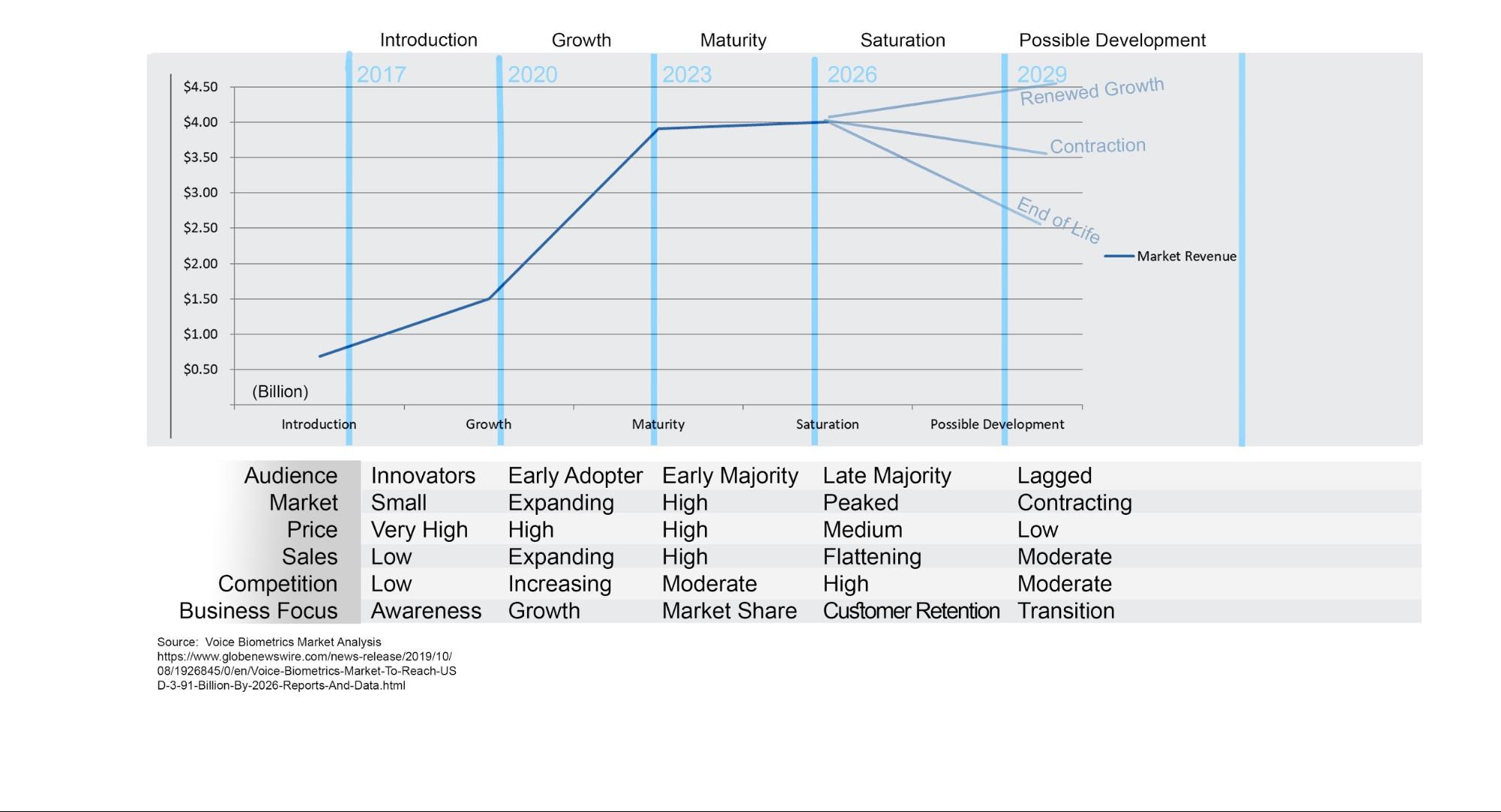
The Voice Biometrics market is both a product of the new age of the Internet of Things and algorithms, and a response to it. It is expected to grow to reach $3.91 Billion by 2026 (see graph below).
For Users: How can companies convince users to adopt a higher level of data security?
Voice Biometrics is part of a global, rolling campaign towards multi-factor authentication, especially as the general public are being made more aware of the value of their data every day.
The motor for this awareness is reporting of data breaches in the media, and the high profile introduction of new laws and regulatory bodies, such as GDPR, as well as the increasing prevalence of algorithm-led tailored services.
The new laws are a response to the unregulated use of data coinciding with a complete integration of digital devices across everyday life- and, subsequently, the steep increase in cyber vulnerabilities.
Adopting levels of data security, and practicing security hygiene will come naturally to those who are learning the value of their data in response to the shifting technological landscape.
Low adoption rates and issues in terms of onboarding is a generational and demographic issue. IBM recently published a study, and found that “Generational differences emerged showing that younger adults are putting less care into traditional password hygiene [using the same password and across multiple domains], yet are more likely to use biometrics, multifactor authentication and password managers to improve their personal security. Older generations showed more care with password creation, but were less inclined to adopt biometrics and multifactor authentication.”
The biggest hurdles to onboarding across all demographics is therefore twofold: addressing the not-unfounded scepticism surrounding the privacy and trust over the actors who collect biometric data, and the onboarding process being part of the seamless technological interaction that people, especially ‘digital natives’ have come to expect and demand.
Voice Biometrics is the natural choice for sceptics, as the collection of voiceprints is done through a process of unilateral encryption- that is to say that the user's voice is analysed by an AI algorithm and recognised as a string of binary data that is as unique as a fingerprint, called a voiceprint. The voiceprint is stored as neutral code that is dissociated from the sound of a person’s voice. It is not possible to recreate any of the enrollment recordings, and therefore the aspect of the identity felt most close to home, from the voiceprint.
Because the other hurdle is offering seamlessness, businesses and services need to encourage users to move from seamless, but now insecure single factor Knowledge-Based authentication, (KBA) to multi-factor authentication using Voice Biometrics. KBA is made seamless through password managers and users using the same password across services.
Read here for our analysis of the weaknesses in KBA
The onboarding process for Voice Biometrics can compete with this seamlessness in two ways. The first is through ‘active’ onboarding- that is to get the user to say a passphrase such as “my voice is my password” for a set number of times to an IVR agent until the algorithm has created a voiceprint in a high enough resolution to be confident in recognising the voice again. The second is through ‘passive’ onboarding- which is gaining consent to use a normal conversation with an agent to create the voiceprint in the same fashion.
The offering of a quick, easy, and highly secure method of moving to Voice Biometrics is an excellent way for businesses that are looking to create key brand differentiation, and gain a high return on investment by, ultimately, enhancing their customer experience.
For Businesses: How do Voice Biometric solutions compare to one another?
It’s a pretty standard microeconomic principle that new technologies enter the market at a premium when they are first made public, until improvements and newer iterations of that technology are created by different people. This in turns creates competition, starts driving the price down, and creates a further need for brand and product differentiation.
What separates the market of Voice Biometric algorithms, however, is that the algorithms themselves have the capacity to learn from experience, which can be capitalised on by the solution providers.
The market of Voice Biometrics is quietly booming, with choice between products. The best way to differentiate products is by looking at four key measures. These are also the standards to which Aculab’s Voisentry is held, making it top-of-its-class, whilst constantly improving in comparison to our competitors.
-
Ease of integration and deployment into existing architectures and APIs
- The Voice Biometric solution must be easily scalable to fit a wide variety of business needs and consumer applications. This means that it should not require an overhaul in terms of platform management, but should have the tenet of easy integration at its core.
- The overhead needed to deploy Voice Biometrics should not need to be channeled out. The solution should be fundamentally integrative and adaptive.
-
Effectiveness of Presentation Attack Detection Algorithm.
- All cybersecurity tools are caught in a kind of cold war between hackers and solution engineers. The Voice biometric solution must therefore have a sophisticated spoof detection feature, to detect bad actors. This is the Presentation Attack Detection Algorithm. Its effectiveness is founded in two types of experience: Experience of the solution providers, with knowledge of the history of hoaxes and hoax detection in the industry; and the experience of the algorithm, having been trained rigorously with a large data set and a deep neural network.
- Look for FIDO certification of the software, an industry standard and validation of good quality in terms of product conformance, interoperability, and data security.
-
Efficacy of the Equal Error Rate (EER): The crossover point of the False Acceptance Rate (FAR) and False Rejection Rate (FRR).
- Allowing an impostor to get into the system is an error of false acceptance. Denying a genuine user access to the system is a false rejection error.
- The Equal Error rate is the crossover point- the mathematical representation of how confident the Voice Biometric algorithm is in allowing access to data, and therefore is directly proportional to how confident businesses can be in the solution being offered!
- There is no industry standard for EER, partly due to the fact that threshold settings and similarity ratings are vendor and implementation specific. However, the EER can only be gained, analysed, and honed by practical deployment of the Voice Biometric solution in a variety of real-world examples. This is what differentiates Voice Biometrics solutions- it is what creates the ability for a solution, such as Voisentry, to be tailored to those specific needs of a variety of businesses and consumer applications, and therefore, forms the third type of experience for a biometric algorithm to become top-of-its-class.
-
Support, Assistance and Customer Service of the Voice Biometric provider.
- Throughout the planning, integration, and deployment phase, the biometric solution provider should assist with the full process of implementation, to tailor the algorithm specifically to business needs.
- The service provider should also be on call to provide technical support and assistance very quickly, much like a locksmith- on-call and with your security and comfort in mind.
Ultimately, Voice Biometrics is a technology that is the result of the collaboration between cryptographers, academic linguists, cybersecurity experts and software engineers. Innovations and differentiation in Voice Biometric algorithms are based on different approaches and theoretical underpinnings- making it a technology that appeals to the inventor in all of us.
Click here to find out more about VoiSentry, or contact us here.
